Data at Rest Encryption Reference Architecture
The following diagram illustrates the supported architecture for deploying Cloudera Navigator encryption for data at rest:
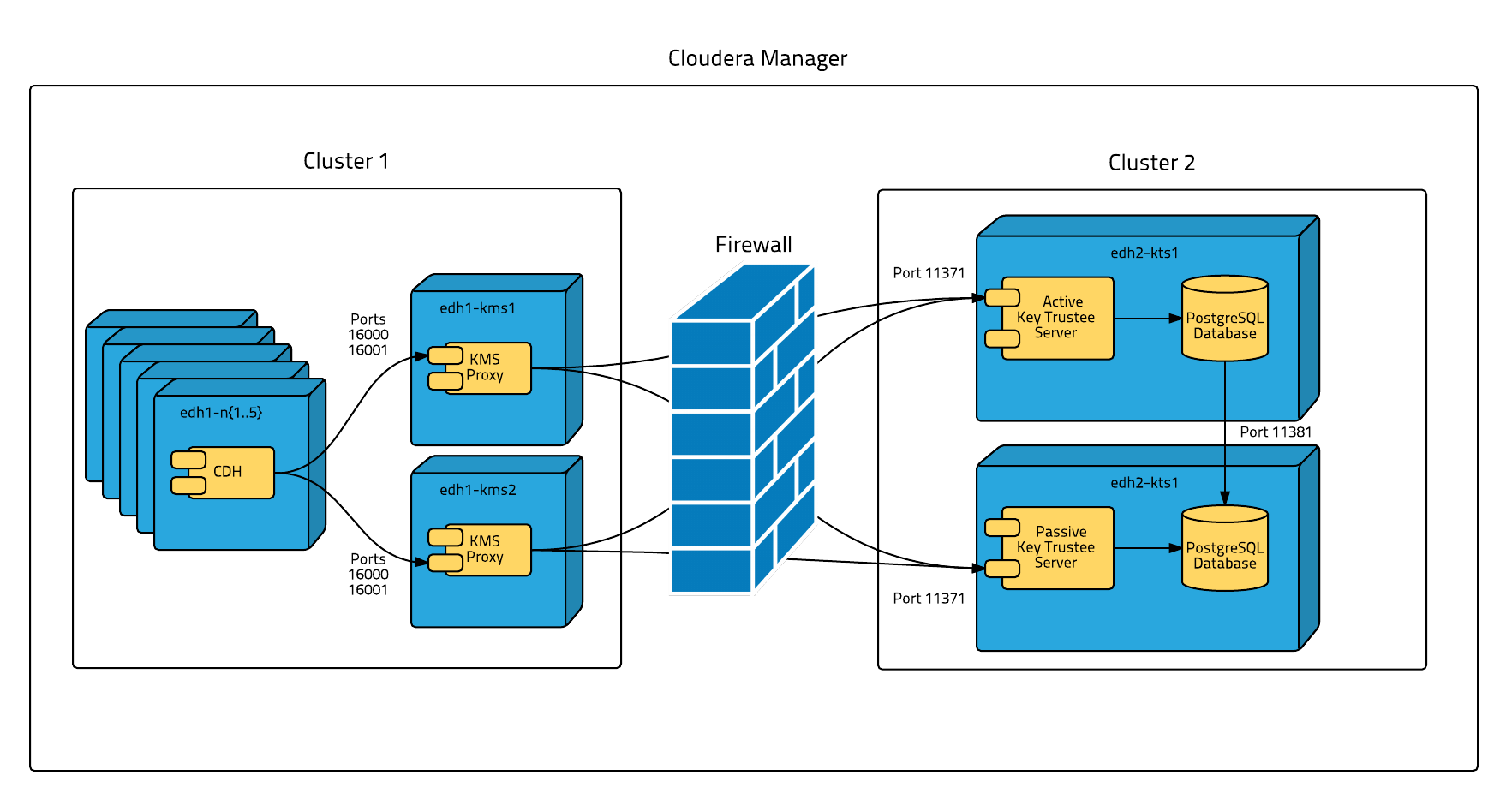
To isolate Key Trustee Server from other enterprise data hub (EDH) services, you must deploy Key Trustee Server on dedicated hosts in a separate cluster in Cloudera Manager. Deploy Key Trustee KMS on dedicated hosts in the same cluster as the EDH services that require access to Key Trustee Server. This provides the following benefits:
- You can restart your EDH cluster without restarting Key Trustee Server, avoiding interruption to other clusters or clients that use the same Key Trustee Server instance.
- You can manage the Key Trustee Server upgrade cycle independently of other cluster components.
- You can limit access to the Key Trustee Server hosts to authorized key administrators only, reducing the attack surface of the system.
- Resource contention is reduced. Running Key Trustee Server and Key Trustee KMS services on dedicated hosts prevents other cluster services from reducing available resources (such as CPU and memory) and creating bottlenecks.
If you are using virtual machines for the Key Trustee Server or Key Trustee KMS hosts, see Navigator HSM KMS HA Planning.
Page generated May 18, 2018.
| << Encrypting Data at Rest | ©2016 Cloudera, Inc. All rights reserved | Data at Rest Encryption Requirements >> |
| Terms and Conditions Privacy Policy |